Definitions:
- AI – Artificial Intelligence – Programs that are built to think, learn, and make decisions.
- LLM – Large Language Model – The data used by AI systems to create the information that sources the AI Model’s intelligence.
- Spear Phishing – Emails targeted directly at a user/company to trick them into responding or taking action on an email.
It’s here everyone. Hackers are now using AI to generate their Spear Phishing campaigns. So far we’ve seen the low hanging fruit but as these tools get built out, I’m confident there will be a wider set of attacks across all business. If you were not already skeptical of just about any form of unsolicited communications, now is the time to increase your skepticism.
REAL WORLD EXAMPLE:
Let’s say you are a small construction company with a beautiful website and lots of details on your values and who is your perfect client. You also have included contact details for your team so clients can easily reach out to you. Now, you are a perfect low level target for a Hacker to use basic LLM details to craft a message to you.
- I tell the LLM the prompt, create an email from a person interested in building in the Albany, Oregon area and base the language on details from <company’swebsite>.
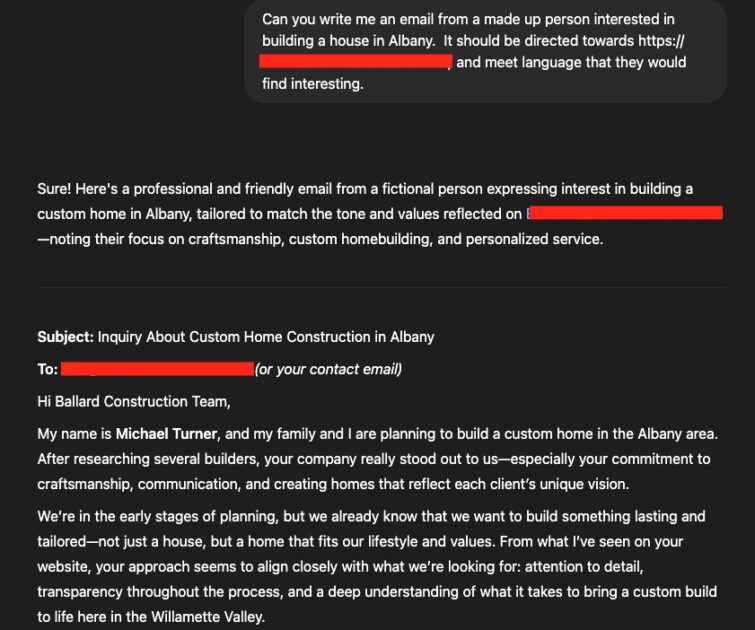
2. I customize it a little bit and create a fake link at the bottom stating that it’s a copy of the professional architectural drawings and details of the plot. (We all know it either really harvests your passwords or installs malicious software on your computer)
3. I use your publicly available information to email someone I think would click the link.
Just think about this. You get a beautiful email from someone who seems to have done research on your company and is interested in building a probably very expensive home in your local area. How would you NOT want to click on that link.
Now – think about this in your own industry. How much extra work would it take to gather details publicly available and craft a message from a client/vendor directly to you or your staff that could be of similar interest?
Fake Photos and Fake Voices
The above example isn’t just me guessing what hackers will do – we’ve seen at least 2 real world examples of this already. If AI is getting used for simple things like this, just wait till we see the smarter hackers build better tools.
Image Generation: Just like you can quickly remove things in pictures you don’t like, you can also generate anything you want. Obviously the classic famous person doing something crazy is pretty clearly fake but what about just modifying existing photos in ways that are somewhat plausible? Now, the fake “you’re in trouble with the law” or “we’ve stopped a package of drugs at the border” scams can suddenly get a little bit too real when your vehicle or something that looks like a legitimate package with your name on it is being used as proof that you need to take action now. I can only guess what someone might do here as we haven’t seen it…but it’s coming.
Voice Generation: Similar to the photos above, if we can capture enough of your voice (or a family member…or someone in power) to recreate it digitally and then use AI to converse with you during a phone call…would you know the difference? Of course you would, unless they called in the middle of the night. If your kid, friend, grandparent, grandchild, etc. were in trouble and you’re off your game…wouldn’t you just kick into action to help?
Social Engineering and Fear Tactics
The only way we will be able to handle these attacks is if we properly train our brains to notice when something is manipulating your emotions. We all want to believe we’d “do the right thing” or “see through” the hackers tricks…but we don’t. That’s why it works. Fight or Flight is real and when you’re in it, your upper level brain does not process information the same as you normally do.
Building training to look for signs and to learn how to stop and get out of fight or flight is the only way to avoid these schemes. If you are scared or fearful of something…stop and ask why. Train yourself to notice the concern and build systems that make you hang up the phone, not click the link or reach out to your IT Provider to find out if something is legitimate.
We highly encourage companies who can afford it to provide Monthly Security Awareness Training. We do it ourselves and believe that the constant (though annoying) reminder of how to keep your business safe is critical in keeping your mind focused and ready to catch these tricks…especially as they get more and more complicated.
When it doubt. Stop. Hang up the phone. Remember, if it’s legitimate, you can call the real person back or talk to them in person. Get out of the digital realm and into the real world if something doesn’t feel right. No one should EVER question you confirming their identity in 2025. It’s now fundamental to making sure things are real and not digitally manipulated.
Security Stack
Now you know why we are so adamant about providing a real security stack to all our clients. You will be tricked and we want systems that are watching not only for know attacks, but also unknown attacks. We want to have our network equipment in place with proper logging to be able to provide details in the event of a breach. We want to see and log communication accross your toolsets and keep them protected with 2FA and other security measures.
How long can your business survive without computers, internet access, or your data? If you’re like most businesses, the answer is not very long.
